I’ve wanted to set up VPN capability to my home network for a while now, in order to gain the benefits of improved security and local network access while working remotely. After a bit of research and some tweaking, I eventually got it working using the following steps.
The type of VPN I chose to use is based on PPTP, rather than the more complex IPSec or L2TP. My primary rationale: I wanted to finish by dinner. Keep in mind, that with the easier implementation of PPTP, one does give up some increased sense of security from the trusted certificate usage and end-end encryption found in IPSEc and L2TP.
Commands:
$ sudo aptitude install pptpd
$ sudo vi /etc/pptpd.conf
#Settings for Otac network – DCato 1/04/14
localip 192.168.2.12
remoteip 192.168.2.234-238,192.168.2.245
$ sudo vi /etc/ppp/pptpd-options
#Settings for Otac network – DCato 1/4/14
ms-dns 192.168.2.1
nobsdcomp
noipx
mtu 1490
mru 1490
sudo vi /etc/ppp/chap-secrets
# client server secret IP addresses
username * secret-password *
Finally, you can reboot the pptpd server with:
$ sudo /etc/init.d/pptpd restart
Edit /etc/sysctl.conf
Un-comment the following line in “/etc/sysctl.conf”:
net.ipv4.ip_forward=1
The following command reloads the configuration (you can also just reboot at the end of this guide):
$ sudo sysctl -p
Open the port on the server:
$ sudo ufw allow 1723
Edit /etc/default/ufw
Edit “/etc/default/ufw” and change the option “DEFAULT_FORWARD_POLICY” from “DROP” to “ACCEPT”
Edit /etc/ufw/before.rules
Add the following either at the beginning of “/etc/ufw/before.rules” or just before the *filter rules (recommended):
# NAT table rules
*nat
:POSTROUTING ACCEPT [0:0]
# Allow forward traffic to eth0
-A POSTROUTING -s 10.99.99.0/24 -o eth0 -j MASQUERADE
# Process the NAT table rules
COMMIT
At this point, you can reset and restart the local firewall:
$ sudo ufw disable && sudo ufw enable
Remember to open up your NAT fireweall as well. This may involve setting up appropriate port forwarding or a DMZ to ensure you can get through to the pptp server on port 1723.
Finally, connecting. On the client side, settings are pretty straight forward – here’s my Android client:
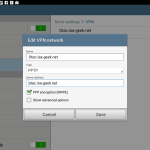
Similar settings would apply for connecting from Windows or other operating systems.